The Hidden Bill: How Shadow IT Quietly Drains Your Security Budget
The CFO's Blind Spot
You've built tight controls around IT spending. You've negotiated enterprise contracts, standardized on approved vendors, and implemented procurement workflows that would make any finance team proud. But here's the uncomfortable truth: a significant portion of your technology spending is happening completely outside your visibility.
Shadow IT, the unauthorized software, tools, and services employees use without IT approval, has evolved from a minor governance headache into a major financial drain. What makes this particularly challenging is that it often masquerades as productivity improvements while quietly undermining your budget discipline and security posture.
The numbers tell a stark story. Recent research indicates that 30–50% of IT spending now occurs outside of IT's control. This isn't just about a few rogue software purchases; it's a systematic shift in how technology gets adopted and paid for across organizations.
The SaaS Subscription Trap
Walk through any department today, and you'll find a maze of overlapping software subscriptions. Marketing uses three different analytics platforms. Sales has signed up for multiple CRM add-ons. HR is paying for recruiting tools that duplicate existing functionality. Each purchase seemed logical in isolation, but collectivel,y they represent a massive waste.
The scale of this problem is eye-opening:
- Mid-size companies: $135,000 per year wasted on unnecessary SaaS tools
- Large enterprises: Up to $7.4 million annually in unused software licenses
- Market-wide impact: $34 billion wasted yearly across U.S. and U.K. companies on unused licensing
These aren't just accounting errors; they're systematic blind spots in how we track and manage technology spending. The costs get buried in departmental budgets, misclassified as general business expenses, or hidden within broader software categories.
The AI Revolution's Dark Side
The explosion in AI adoption has created an entirely new category of shadow spending. Employees are integrating generative AI tools into their daily workflows at an unprecedented pace, often without any oversight from IT or legal teams.
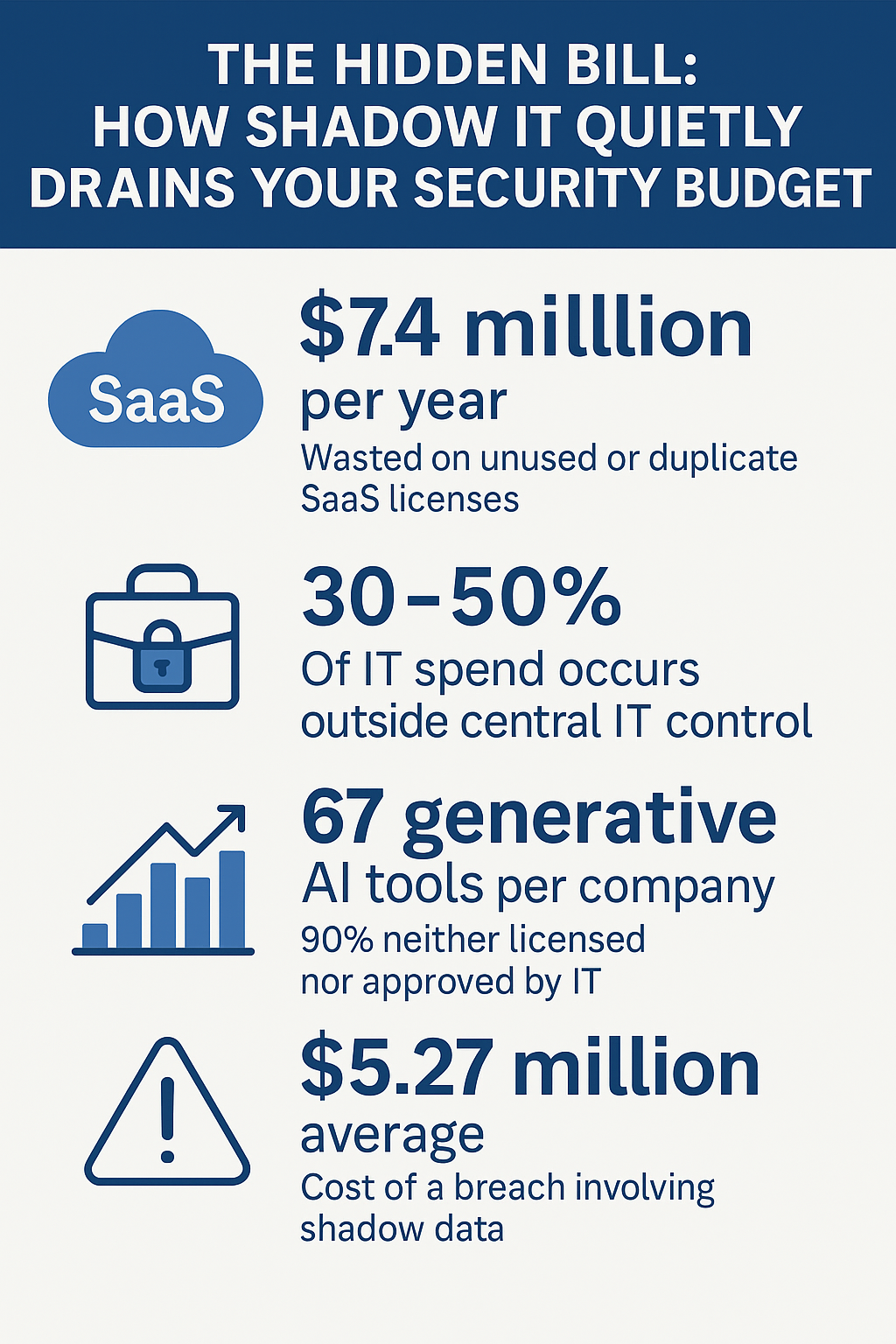
Consider these findings that should concern any CFO:
- 67 generative AI tools used by the average company (90% unsanctioned)
- 50% of employees regularly use unapproved AI tools
- 27.4% of AI prompts now include sensitive or regulated data
This creates multiple financial exposures. There are the obvious costs, API usage fees, premium subscriptions, and productivity tool add-ons that employees expense or charge to departmental budgets. But the hidden costs are potentially much larger: regulatory exposure under GDPR, CCPA, and HIPAA; legal liabilities when intellectual property gets inadvertently shared with third-party AI services; and the operational overhead of managing dozens of point solutions instead of a cohesive AI strategy.
Many of these tools operate under consumer-grade terms of service, which means your company may have limited recourse if something goes wrong. That's a risk most CFOs would never knowingly accept, yet it's happening by default across organizations.
When Shadow IT Meets Security Incidents
Security breaches are expensive under any circumstances, but they become significantly more costly when shadow systems are involved. When your IT and security teams don't know about certain tools or data repositories, they can't protect them effectively.
The financial impact is substantial:
- $5.27 million: Average cost of breaches involving shadow systems
- 20% longer: Time required to contain these incidents
- 26% longer: Time needed to detect shadow IT-related breaches
- 30-50%: Portion of all security incidents now involving shadow IT
From a finance perspective, these events trigger cascading costs that are difficult to predict or budget for: emergency vendor engagements, specialized legal and PR consulting, regulatory fines, mandatory compliance audits, and revenue losses from operational downtime or damaged customer trust.
The Compound Effect of Inefficiency
Beyond the dramatic costs of breaches and unused licenses, shadow IT creates ongoing operational inefficiencies that compound over time. When departments make technology purchases in isolation, your organization loses negotiating leverage with vendors. Enterprise-wide discounts become impossible when usage is fragmented across dozens of individual subscriptions.
Staff time gets wasted on boarding and troubleshooting redundant or incompatible tools. IT teams find themselves supporting unfamiliar platforms after the fact, leading to longer resolution times and increased support overhead. Integration projects become more complex when they need to account for tools that weren't part of the original architecture.
These inefficiencies are harder to quantify than direct software costs, but they represent a real drag on productivity and team effectiveness

Bringing Shadow IT Into the Light
Addressing this challenge requires more than just better policies—it requires better visibility. You can't manage what you can't see, and traditional IT monitoring tools often miss the full scope of shadow technology usage.
This is where solutions like InnerActiv become valuable. Unlike network-based monitoring that only sees traffic patterns, endpoint-level visibility provides the context needed to understand how technology is actually being used.
This includes identifying unused or underutilized software licenses across the enterprise, helping finance teams recover wasted spending and make more informed renewal decisions. It means detecting unauthorized or unapproved tools, even those that operate outside traditional network monitoring. Most importantly for today's environment, it includes flagging interactions with unsanctioned AI tools and APIs, particularly when sensitive data is being shared with external services.
This kind of comprehensive visibility transforms IT governance from a reactive compliance exercise into proactive financial management.
A Finance-Led Response
Shadow IT represents a business challenge that extends well beyond IT's traditional scope. CFOs are uniquely positioned to drive the organizational changes needed to address it effectively.
Immediate Actions for CFOs:
- Demand comprehensive visibility – Partner with IT to implement discovery tools that identify SaaS usage, AI interactions, and API connections across the organization
- Create dedicated budget tracking – Establish specific line items for shadow IT analysis and remediation to make costs visible and create accountability
- Establish AI governance policies – Require enterprise-grade contracts for any generative AI tools, with explicit controls around data usage, processing, and storage
- Tighten procurement controls – Limit expense reimbursements for unapproved tools and route all technology purchases through centralized evaluation
- Build executive reporting – Create dashboards showing unused license spending, AI exposure levels, and financial impact of shadow IT-related security incidents
The Financial Imperative
Shadow IT has evolved from a minor IT governance issue into a significant financial challenge. With AI adoption accelerating and software sprawl continuing to increase, the costs and risks will only grow larger.
As a CFO, you have the authority and perspective needed to address this systematically. The goal isn't to eliminate all unauthorized technology use; that's neither realistic nor desirable. Instead, it's about creating visibility, establishing appropriate controls, and ensuring that technology spending aligns with business objectives and risk tolerance.
The companies that address shadow IT proactively will find themselves with cleaner budgets, stronger security postures, and more strategic technology investments. Those that don't will continue to see their technology spending erode through a thousand small cuts, each one seemingly insignificant until viewed in aggregate.
The choice is clear: shine a light on shadow IT spending now, or continue paying the hidden bill indefinitely.

Zero Trust Meets Its Biggest Adversary: AI
AI is now embedded into daily work. It generates content, analyzes data, interacts with internal systems, and increasingly performs tasks on behalf of employees. This shift delivers enormous productivity gains, but it also breaks the assumptions that make Zero Trust possible.

AI Agents: The 2026 Insider Threat You Can't Ignore
In 2026, the next major insider threat isn't just human—it's AI agents operating at machine speed with broad permissions and limited oversight. For years, insider threat programs have focused on people: disgruntled employees, compromised credentials, and simple human error. That definition is breaking down fast.










